Fundamental
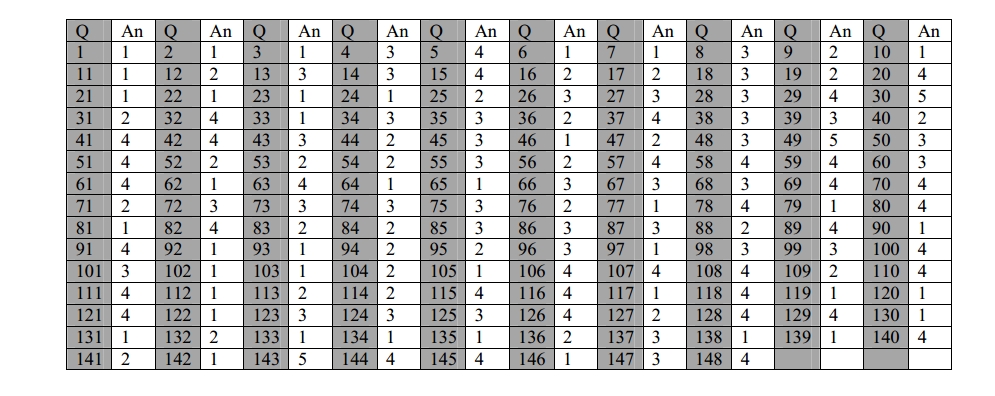
1. SMPS stands for
1) Switched mode power supply
2) Start mode power supply
3) Store mode power supply
4) Single mode power supply
2. BIOS stands for
1) Basic Input Output system
2) Binary Input output system
3) Basic Input Off system
4) all the above
3. The father of Modern Computer is
1) Charles Babbage 2) Von-nuumann 3) Danies Ritchel 4) Blaise
Pascal
4. How many options does a BINARY choice offer
1) None 2) One 3) Two
4) it depends on the amount of memory on the computer
5. How many values can be represented by a single byte?
1) 4 2) 16 3) 64 4) 256 5) 512
6. IT stands for—
1) information Technology
2) integrated Technology
3) intelligent Technology
4) interesting Technology
7. CAD stands for
1) Computer aided design
2) Computer algorithm for design
3) Computer application in design
4) All of the above
8. IBM stands for
1) Internal Business Management
2) International Business Management
3) International Business Machines
4) Internal Business Machines
9. Which of the following refers to the fastest, biggest and most
expensive computers ?
1) Personal Computers
2) Supercomputers
3) Laptops
4) Notebooks
10. An error is also known as—
1) Bug 2) Debug 3) Cursor 4) Icon
11. Which is the part of a computer that one can touch and
feel?
1) Hardware 2) Software 3) Programs 4) Output
12. ________ are specially designed computer chips reside inside
other devices, such as your car or your electronic
thermostat.
1) Servers
2) Embedded computers
3) Robotic computers
4) Mainframes
13. The following are all computing devices , except………
1) notebook computers
2) cellular telephones
3) digital scanners
4) personal digital assistants
14. ________ controls the way in which the computer system
functions and provides a means by which users can
interact with the computer
1) The platform
2) Application software
3) Operating system
4) The motherboard
15. A database management system (DBMS) is a …………
1) hardware system used to create , maintain and provide controlled
access to a database
2) hardware system used to create, maintain, and provide
uncontrolled access to a database.
3) software system used to create, maintain, and provide
uncontrolled access to a database.
4) software system used to create, maintain, an d provide
controlled access to a database.
16. _____ are words that a programming language has set aside for
its own use.
1) Control worlds 2) Reserved words 3) Control structures 4)
Reserved keys
17. Granting an outside organization access to internet web pages
is oft en implemented using a (n) __
1) extranet 2) intranet 3) internet 4) hacker
18. Chip is a common nickname for a (n):
1) transistor 2) resistor 3) integrated circuit 4)
semiconductor
19. A _________ contains specific rules and words that express the
logical steps of an algorithm.
1) programming language
2) syntax
3) programming structure
4) logic chart
20. The most frequently used instructions of a computer program are
likely to be fetched from:
1) the hard disk 2) cache memory 3) RAM 4) registers
21. The ____________ contains data descriptions and defines the
name, data type, and length of each field in the
database.
1) data dictionary 2) data table 3) data record 4) data field
22. The _____ manual tells you how to use a software program.
1) documentation 2) programming 3) technical 4) user
23. _________ is the process of finding errors in software
code.
1) Debugging 2) Compiling 3) Testing 4) Running
24. Linux is a (n) ____________ operating system.
1) open-source 2) Microsoft 3) Windows 4) Mac
25. What is a backup?
1) Restoring the information backup
2) An exact copy of a system’s info rmation
3) The ability to get a system up and running in the event of a
system crash or failure
4) All of these
26. Which of the following places the common data elements in order
from smallest to largest
1) character, file, record, field, database
2) character, record, field, database, file
3) character, field, record, file, database
4) Bit, byte, character, record, field, file, database,
27. When you purchase a product over a Mobile Phone, the
transaction is called
1) Web Commerce 2) e-Commerce 3) m-Commerce 4) Mobile
Purchases
28. A Pixel is –
1) A computer program that draws picture
2) A picture stored in secondary memory
3) The smallest resolvable part of a picture
4) None of these
29. Algorithm and Flow chart help us to
1) Know the memory capacity
2) Identify the base of a number system
3) Direct the output to a printer
4) Specify the problem completely and clearly
30. Modern computers represent characters and numbers interally
using one of the following number
systems._________
1) Penta 2) Octal 3) Hexa 4) Septa 5) Binary
31. Minimize window, what it will do?
1) Close the window
2) Make it an icon and store on task bar
3) Close window after saving its contents
4) Shut down the computer
32. It is a smallest dot that can be uniquely drawn on a computer
screen. This is called
1) Boxel 2) Computer Dot 3) Cursor 4) Pixel
33. A computer that combines the characteristic of analog and
digital computer
1) Hybrid Computer 2) Digital Computer 3) Analog Computer 4) Super
Computer
34. Capability of computer to perform more than one tasks at the
same time is
1) Batch Processing 2) Real Time processing 3) Multitasking 4)
Scheduled Processing
35. The screen background is known as the
1) Application 2) Window 3) Desktop 4) Frames
36. A(n) _______ uses pictures (called icons) and menus displayed
on the screen to send commands to the
computer system.
1) command - based user interface
2) GUI
3) system utility
4) API
37. Which amount them is not an application software
1) Ms word 2) Ms Excel 3) Adobe Acrobat 4) Turbo C complier
38. Display bar that list all the open folders and active
application is
1) Menu bar 2) Tool Bar 3) Task Bar 4) Window List
39. VIRUS stands for
1) Very Important Record user Searched
2) Verify Interchanged result until source
3) Virtual Information Resource Under Seize
4) Very Important Resource Under Search
40. Active Window means
1) The active windows is designated by a different color
toolbar
2) The window that is currently open.
3) Both a and b above mentioned 4) The windows that is last
used
41. A bitmap is
1) Is a format which windows use for desktop wall paper
2) A graphic file format made up of small dots.
3) A specific kind of bitmap file with the .BMP extension
4) All of the above
42. Java is a
1) Compiler 2) Operating System 3) Input Device 4) Programming
Language
43. What is JVM?
1) Jumber Verbose Mechanics
2) A part of IIS
3) Java Virtual Machine
4) .Net Framework
44. A computer programmer
1) Enters data into computer
2) Writes programs
3) Changes flow chart into instruc tions
4) Does total planning and thinking for a computer
45. Who invented the super-computer?
1) P.T Farnsworth 2) J.R Whinfield 3) J.H. Van Tassell 4) Charles
Ginsberg
46. Which supercomputer is developed by the Indian
Scientists?
1) Param 2) Super 301 3) Compaq Presario 4) CRAY YMP
47. IC chips used in computer are usually made of
1) Lead 2) Silicon… 3) Chromium 4) Gold
48. Time during which a job is processed by the computer is
1) Delay time 2) Real time 3) Execution time 4) Down time
49. A collection of related fields in data organization is
called.
1) Group 2) File 3) Information 4) Register 5) Record
50. _________are lists of commands that appear on the screen.
1) GUIs 2) Icons 3) Menus 4) Windows
51. “Buy Now- Pay Now” is commonly use for ____________
1) Visa Cards 2) Credit Cards 3) E-purse 4) Debit Cards
52. ____Granting an outside organization access to internet web
pages is often implemented using a(n)
1) Extranet 2) Intranet 3) Internet 4) Hacker
53. ___________means that the data contained in a database is
accurate and reliable.
1) Data redundancy 2) Data integrity 3) Data reliability 4) Data
consistency
54. CAD software is most likely to be used by:
1) Web designers. 2) engineers. 3) project managers. 4) magazine
editors.
55. The smallest unit of information in a database is called
a:
1) Byte. 2) record. 3) field. 4) cell.
56. In a database of employees, all the information about a
particular person would constitute a:
1) file. 2) record. 3) field. 4) table.
57. A table is a collection of:
1) Files. 2) Worksheets. 3) Fields. 4) Records
58. Computers process data into information by working exclusively
with:
1) multimedia. 2) words. 3) characters. 4) numbers
59. In the binary language each letter of the alphabet, each number
and each special character is made up of a
unique combination of:
1) eight bytes. 2) eight kilobytes. 3) eight characters. 4) eight
bits
60. Computers use the language to process data.
1) Processing 2) Kilobyte 3) Binary 4) Representational
61. Viruses, Trojan horses and Worms are
1) able to harm computer system
2) unable to detect if affected on computer
3) user-friendly applications
4) harmless applications resident on computer
62. A computer with CPU speed around 100 million instructions per
second & with the word length of around 64
bits is known as
1) Super computer 2) Mini computer 3) Micro computer 4) Micro
computer
63. In a database ________ fields store numbers use to perform
calculation
1) Next 2) Key 3) Alphanumeric 4) Numeric
64. In database a filed is ___________
1) Label
2) Table of information
3) Group of related records
4) Category of information
65. The four main functions of a computer are:
1) Input, processing, output, and storage.
2) Learning, thinking, intelligence, and virtuosity.
3) Data, information, bits, and bytes.
4) Hardware, software, modeling, and operations.
66. User actions such as keystrokes or mouse clicks are referred to
as:
1) Interrupts. 2) Tasks. 3) Events. 4) Processes
67. Which of the following is NOT one of the four major data
processing functions of a computer?
1) gathering data
2) processing data into information
3) analyzing the data or information
4) storing the data or information
68. The ability to recover and read deleted or damaged files from a
criminal's computer is an example of a law enforcement specialty
called:
1) robotics. 2) simulation. 3) computer forensics. 4)
Animation
69. Which of the following statements is FALSE concerning file
names?
1) Files may share the same name or the same extension but not
both
2) Every file in the same folder must have a unique name
3) File extension is another name for file type
4) The file extension comes before the dot (.) followed by the file
name
70. To locate a data items for storage is
1) Field 2) Feed 3) Database 4) Fetch
71. Off-line operation is the operation of devices without the
control of
1) Memory 2) CPU 3) ALU 4) Control unit
72. Wild card operators specifies
1) can be used when writing into multiple files
2) allows several files to be read simultaneously
3) Provide an easy way of groups of related files
4) Are only used when printing the contents of a file
73. Accessing records from a file directly without searching from
the beginning of the file is
1) Time sharing 2) Random 3) Direct access 4) Access time
74. Which of the following is not a usual file extension in
DOS?
1) .EXE 2) .BAT 3) .o 4) .class
75. Which of the following is not a part of a standard office
suit?
1) File Manager. 2) Image Editor 3) Database 4) Word
Processor
76. A_________is a bi-stable electronic circuit that has two stable
states.
1) Multivibrator 2) Flip-flop 3) Logic gates 4) Laten
77. The power-saving mode that allows the computer to be restarted
by simply pressing a key on the keyboard is called:
1) standby. 2) warm boot. 3) power management. 4) cold
boot.
78. _________is the science that attempts to produce machines that
display the same type of intelligence that humans do.
1) Nanoscience 2) Nanotechnology 3) Simulation 4) Artificial
intelligence (AI)
79. A spooler is a(n):
1) location in memory that maintains the contents of a document
until it prints out.
2) print job.
3) program that coordinates the print jobs that are waiting to
print.
4) message sent from the printer to the operating system when a
print job is completed.
80. The____button on the quick access Toolbar allows you to cancel
your recent commands or actions.
1) Search 2) Cut 3) Document 4) Undo
81. Many times we read a term CBS used in banking operation. What
is the full form of the letter ‘C’ in the term
‘CBS’?
1) Core 2) Credit 3) Continuous 4) Complete
82. Which device can understand difference between data &
programs?
1) Input device 2) Output device 3) Memory 4) Microprocessor
83. When a key is pressed on the keyboard, which standard is used
for converting the keystroke into the corresponding bits
1) ANSI 2) ASCII 3) EBCDIC 4) ISO
84. Direct X is a _____
1) Computer Part
2) Software that drives Graphic hardware
3) A User Interface
4) None of these
85. The portion of the CPU that coordinates the activities of all
the other computer components is the
1) Motherboard
2) Coordination board
3) Control unit 4) Arithmetic and logical
unit
86. ____________ are lists of commands that appear on the
screen.
1) GUIs 2) Icons 3) Menus 4) Windows
87. Verification of a login name and password is known as:
1) Configuration 2) Accessibility 3) Authentication 4) logging
in
88. A (n)………contains commands that can be selected.
1) Pointer 2) Menu 3) Icon 4) Button
89. When data changes in multiple lists and all lists are not
updated, this causes:
1) data redundancy
2) information overload
3) duplicate data
4) data inconsistency
90. Taking back-up of a file against crash is a
1) Preventive measure
2) Curative measure
3) Decisive measure
4) None of these
91. Most dangerous risk in leaking of information is :
1) Ready access to online terminals
2) Online processing of data
3) Ignorance about the existence of risk
4) All of these
92. An online transaction is
1) One that is done in real time
2) Transaction done via internet
3) One that is done via telephone
4) None of these
93. A clerk in a bank has to access data n customer account.
Logical access control for these users would be.
1) Use of individual passwords
2) Use of an Accounts Receivable Section password
3) Use of individual passwords plus separate access passwords for
customer data and product data
4) Can't say
94. To stop unauthorized access to the computer system we
should
1) Have a trustworthy system administrator
2) Have a good passwords policy
3) Have a sound encryption policy
4) All of the above
95. Which of the following is single user computer with many
features and good processing power?
1) Minicomputer 2) Workstation 3) Macintosh 4) None of these
96. The circuitry that includes the CPU and memory chips is located
on the:
1) System unit. 2) Operating system. 3) Motherboard. 4) Computer
platform.
97. Which number system is usually followed in a typical 32-bit
computer?
1) 2 2) 10 3) 16 4) 32
98. A collection of related information sorted and dealt with as a
unit is a—
1) Disk 2) Data 3) File 4) Floppy
99. How is power supplied to a low-power USB device?
1) Through a power cable
2) From an external power supply
3) Directly from the computer's power supply
4) Through the USB cable
100. The time it takes a device to locate data and instruction and
make them available to the CPU is known as
1) Clock speed 2) A processing cycle 3) CPU Speed 4) Access
time
101. Which menu is present in WordPad but not present in
notepad?
1) Edit 2) File 3) Insert 4) View
102. ASCII stands for
1) American Standard Code for information interchange
2) American Statistical code for information interchange
3) Alphabetic series code for information interchange
4) Alphabetic Standard code for information interchange
103. What is the hex value of decimal number 15?
1) F 2) 1 3) 0 4) E
104. If you want to copy a selection of text, which of button do
you click?
1) Move 2) Copy 3) Duplicate 4) Cut
105. Computer use _________ number system
1) Binary 2) Octal 3) Hexadecimal 4) Decimsl
106. A computer system includes ………………….
1) Hardware 2) Software 3) Peripheral devices 4) All of the
above
107. Which one of the following is not hardware?
1) Magnetic Tape 2) VDU terminal 3) Printer 4) Assembler
108. The number system that is the basis for computer operation
as
1) Hexadecimal System 2) Octal System 3) ASCII 4) Binary
System
109. On which button does help menu exist?
1) End 2) Start 3) Turn Off 4) Restart
110. File extension are used in order to
1) Name of file
2) Ensure the filename is not lost
3) Identify the file
4) Identify the file type
111. The simultaneous processing of two or more programs by
multiple processors is __________
1) Multiprogramming 2) Multitasking 3) Time sharing 4)
Multi-processing
112. Which is not a basic function of a computer?
1) Copy text 2) Accept input 3) Process data 4) Store data
113. Which of the following is part of the system Unit?
1) Monitor 2) CPU 3) CD-ROM 4) Floppy Disk
114. A UPS________
1) Limits damage caused by fluctuati ng level of
electricity
2) Provides battery backup for a limited time
3) Delivers electronic messages via a bus
4) Conducts a power on self test, or POST
115. The information you put into computer is called
1) Facts 2) Files 3) Directory 4) Data
116. The name of the computer’s brain s
1) ROM 2) RAM 3) ALU 4) CPU
117. All the deleted files go to _______
1) Recycle Bin 2) Task Bar 3) Tool bar 4) My Computer
118. A directory within a directory is called
1) Mini Directory 2) Janitor Directory 3) Part Directory 4) Sub
Directory
119. The main directory of a disk is called the __________
directory
1) Root 2) Sub 3) Folder 4) Network
120. The name given to a document by user is called
1) Filename 2) Program 3) Data 4) Record
121. Date and Time are available on the desktop at ____-1) Keyboard
2) Recycle Bin 3) My computer 4) Task bar
122. A personal computer is designed to meet the computer need of
a(n)
1) Individual 2) Department 3) Company 4) City
123. Printed information, called _____ exists physically and is a
more permanent from of output than that
presented on a display device.
1) Soft Copy 2) Carbon Copy 3) Hard Copy 4) Desk Copy
124. A ___ is an icon on the desktop that provides a user with
immediate access to a program or file
1) Kernel 2) Buffer 3) Shortcut 4) Spooler
125. A place that a user can create to store files__________
1) Cursor 2) Text 3) Folder 4) Boot
126. What is the full form of USB as used in computer related
activiti es?
1) Universal Security Block
2) Ultra Serial Block
3) United Service Block
4) Universal Serial Bus
127. You organize files by storing them in ………..
1) Archives 2) Folders 3) Indexes 4) Lists
128. Where is the disk put in a computer?
1) In the modem 2) In the hard drive 3) Into the CPU 4) In the disk
drive
129. ________ is the process of carrying out commands.
1) Fetching 2) Storing 3) Decoding 4) Executing
130. The basic goal of computer process is to convert data
into
1) Information 2) Tables 3) Files 4) Graphs
131. Choices are referred to as_______
1) Options 2) Exit 3) Boot 4) Folder
132. A fault in a computer program which prevents it from working
correctly is known as
1) Boot 2) Bug 3) Biff 4) Strap
133. Which one of the following allows users to continue to operate
computers while printing is in progress?
1) Spooler
2) Job Control Program
3) Os Supervisor
4) None of these
134. When you are working on a document on a PC, where is the
document temporarily stored?
1) RAM 2) ROM 3) The CPU 4) Flash memory
135. Saving is the process
1) To copy document from memory to storage
2) To change the content of any document
3) To change the display or entire document
4) To develop document by entering text using
keyboard
136. Processing involves:
1) Inputting data into a computer system
2) Transforming input into output
3) Displaying output in a useful manner
4) Providing relevant answers
137. A _______ is a unique name that you give to a file of
information
1) Device letter 2) Folder 3) Filename 4) Filename extension
138. Every component of your computer is either ________ or
________
1) Hardware or software
2) Software or CPU/RAM
3) Application software
4) Input devices or output devices.
139. IN Ms-Access, a table can have ____ primary key/keys
1) One 2) Two 3) Three 4)
Four
140. The ability to find an individual item in a file immediately
____ is used.
1) File allocation table 2) Directory 3) Sequential access 4)
Direct access
141. Which of the following is NOT a hardware of a computer
1) Monitor 2) Windows 3) Key board 4) CPU
142. A commonly use graphic format for the web is
1) GIF 2) BMP 3) TEXT 4) IMP 5) TIFr

Banking terms with basic explanations
Financial terms with basic explanations and examples
How to prepare for any interview
UNESCO World heritage sites in India
Excellent video on everyone having something special
Best computer awareness question bank
Subjective topics and tips for SBI Associate PO
Maths various questions for practice
Various vacancies in Govt general insurance
20 lakh vacancies in Indian banking sector
Basic questions for banking interview